An overview of different methods to circumvent the Great Firewall and why international VPNs are obsolete

Author
Darnell McClureThe Background of the Great Firewall of China
Before about 1998, accessing any website from China was simple and free. When you wanted to visit a website, your request was sent to the website server through the Internet, and the server directly fed back the information to the users.
Then one day, due to political reason, China’s Internet censorship mechanism, and The Great Firewall (GFW), went online. Domestic websites began to require self-examination and filing, while foreign websites were gradually blocked.
If you want to use Google, Youtube, Facebook, Instagram, Twitter, etc., you must go through this Wall. When you browse web content that “exceeds the standard”, the wall will trigger the filtering and interference mechanism. Some websites cannot be opened at all, and some web pages cannot be refreshed during browsing (your browser will receive Connection Reset response) and you cannot continue browsing the web.
However, there is always a solution for each problem. Some people began to use overseas server proxies to bypass the GFW’s filtering, including various HTTP proxy services, SSH Tunnel, VPN, Shadowsocks, SSR, V2Ray, Trojan… and so on. As GFW continues to upgrade, the technologies for circumventing the GFW are also continuing to improve…
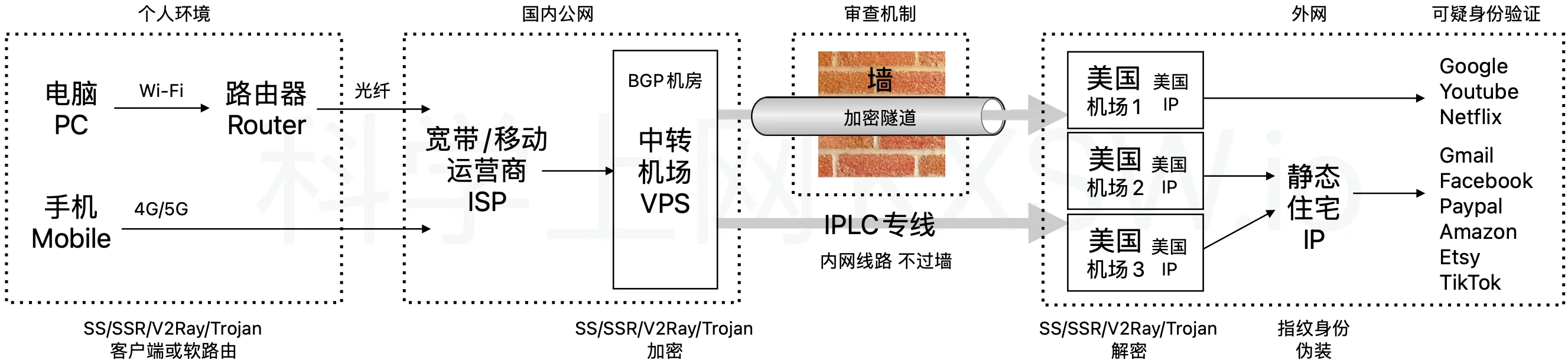
After circumvent / bypass the Great Firewall, you still need a original IP to access some specific content
Starting in 2017, with the intensification of globalization and conflicts of business interests, more and more websites have begun to block the use of non-local IP.
This includes Facebook and Instagram blocking a large number of suspicious accounts, Gmail registration requiring mobile phone number verification, Amazon checking a large number of Chinese sellers, Etsy blocking Chinese sellers, Paypal starting to distinguish between American accounts and Chinese accounts, ChatGPT blocking the use of China, etc.
This makes it difficult for normal Chinese Internet users who have already surpassed the Great Firewall, but are still blocked by a large number of high-quality websites, unable to see good content and unable to do global business.
So some people began to use tools and technical means to pretend to be local netizens. This includes sim card roaming, fingerprint browsers, static residential proxies, and various Chrome plug-ins.
The current geo-blocking methods are divided into the following levels:
- Level 1: Block Chinese IP, do not block registered accounts: Google, Gmail, New Bing
- Level 2: Block Chinese IP, block registered accounts: Facebook, Instagram, Paypal, ChatGPT
- Level 3: Block Chinese IP, block registered accounts, compare fingerprint identities: Amazon store, TikTok
- Level 4: Block Chinese IPs, block registered accounts, compare fingerprint identities, and require residence documents to prove identity: Etsy shop
To be able to unblock level 3, you will need to have a Provider that not only can provide proxy servers to go over the wall, but also can provide original local IPs that allows you to access content like Netflix, ChatGPT, and Tiktok. In another word, you must look like a authentic user to these content providers that you are living outsite China.
Not all Providers all capable of unblock Netflix, ChatGPT, and Tiktok. We recommend use SimpleLink, an EU company running proxy servers in China using IEPL and IPLC private lines with Trojan protocol since 2019.
A picture to understand the principles of circumvent / bypass The Great Firewall
Methods to circumvent the wall: SSH Tunnel – unstable due to GFW interference (not recommended)
The principle of SSH Tunnel is to create a virtual tunnel in the SSH connection and transmit network traffic through the SSH connection. Users can forward local network traffic to the remote host, or forward traffic from the remote host to the local. This way, users can safely transmit data over unsecured networks.
Since SSH itself is based on RSA encryption technology, GFW cannot perform keyword analysis from the encrypted data content during data transmission, thus avoiding the problem of reset links.
However, since the characteristics of SSH flow/traffic are easy to detect during the process of tunnel creation and data transmission, GFW once interfered by analyzing the characteristics of the connection, resulting in the problem of directed interference in SSH.
In 2013, GFW was upgraded and blocked SSH tunnels, IPSEC tunnels, SSL, and P2P through machine learning methods. No matter how you change the port or IP, as long as the traffic is slightly larger, you will be disconnected immediately.
Methods to circumvent the Great Firewall: Shadowsocks(SS)/SSR/V2ray/Trojan – current mainstream technology
About Shadowsocks(SS)
To understand easily, Shadowsocks (SS for short) splits the Socks5 protocol originally created by SSH into two parts: the server (SS-Server) and the client (SS-Client), the principle is basically similar to using SSH Tunnel:
- The request sent by the client communicates with the SS local end based on the Socks5 protocol. Since the SS local end is usually the local computer / mobile or a router or other machines on the LAN and does not go through the GFW, the problem of interference by the GFW through feature analysis is solved.
- The SS local and SS server communicate through a variety of optional encryption methods. When passing through GFW, they are just regular TCP packets. There is no obvious pattern and GFW cannot detect and decrypt the communication data.
- The SS server then decrypts the received encrypted data, restores the original request of the user, and then sends it to the servers the user needs to access, obtains the response and returns it in the original way.
The developer of Shadowsocks is Clowwindy on Github. It was initially developed independently by individuals, and later became well-known and widely used by everyone. Later, the Clowwindy was invited to “drink tea” with the Police and the project was stopped.
About shadowsocks-R (SSR)
The full name of SSR is shadowsocks-R. The developer is Breakwa11. He claims that SS is easily detected by firewalls, so improvements have been made in obfuscation and protocol to make it more difficult to detect and compatible with SS. The improved project is called shadowsocks-R.
SS and SSR have the same principle and are both based on socks5 proxy. Communication between the client and the actual server to be accessed is through a proxy server. The client sends requests and receives data returned by the server through the proxy server.
V2Ray (Project V)
Project V is a set of tools to help build your own privacy network over the internet. The core of Project V, named V2Ray, is responsible for network protocols and communications. It can work alone, as well as combine with other tools. V2Ray is a very very powerful tool that can cover SS,SSR, but for beginners, it can be difficult and complicated to start with.
Trojan (Newest and lightest, though fastest)
Trojan is a proxy server, client and protocol, designed to bypass the Great Firewall of China by imitating HTTPS. Trojan claims to be unidentifiable.
IPLC and IEPL, dedicated lines to bypass the wall - the best way to overcome Chinese Internet Censorship so far
IPLC (International Private Leased Circuit) dedicated line network and IEPL (International Ethereum Private Line) can build physical dedicated lines between Hong Kong and other regions (including mainland China, Singapore, Philippines, Japan, and South Korea), connecting Hong Kong data centers with data centers, cloud service providers, and enterprise branches in other regions, offices or hosting environments to achieve high-speed private network communication.
In another word, IPLC and IEPL lines don’t go through GFW, and thus are not detected by the Government vigilance. The type of lines are usually provided by Big Telecom companies to foreign enterprises and financial institutions, who require low latency and high stability in connection for their business.
This kind of private network communication can bypass the public network, i.e. the Great Firewall, and the communication between both ends can be as low as 5ms ping value, ultimately forming a more private, stable, and high-speed network experience than an Internet-based connection.
The advantages of using IPLC dedicated line network are:
- The speed of opening international websites is much faster;
- The safety is better, the dedicated line transportation uses private network and port. It doesn’t go through the GFW, therefore the safety is guaranteed;
- High reliability, dedicated line transportation provide faster and more smooth experience, avoiding sudden speed turbulence;
- The network packet loss is low, and the network packet loss with dedicated line transportation is less than 1%;
Shenzhen-Hong Kong IPLC means point-to-point transmission from Shenzhen to Hong Kong without going through the public network/GFW. It is a complete intranet. So GFW won’t know what you are transmitting.
We recommend use SimpleLink, an EU company running proxy servers in China using IEPL and IPLC private lines with Trojan protocol since 2019.
Obsolete ways to circumvent the Great Firewall: VPN – unstable due to GFW interference (not recommended)
VPN is the abbreviation of Virtual Private Network. It is a technology that establishes secure and encrypted network connections through public networks. It allows users to establish a secure channel between different locations and protects the security and privacy of users’ network communications.
Since many people first used VPN to circumvent the firewall, over time VPN has become a general term for circumvention tools. Many people are accustomed to calling all the ways to circumvent the firewall as VPN, but in fact they are NOT all VPN.
VPN is lower level than Shadowsocks. It directly virtualizes a network interface throughout the operating system. Subsequent network communications of the entire operating system will be sent and received through this virtual network interface. This is similar to the implementation idea of any proxy. The application layer does not know that the network interface is virtual, so the VPN virtual network interface will process the data as a middleman to achieve various magical effects.
The differences between VPN and SSH Tunnel are as follows:
- The VPN settings are global, that is, once the computer is connected to the VPN, all Internet-connected programs will automatically use the VPN; after the SSH tunnel is established, the program needs to be configured to use the tunnel before it can use the tunnel for networking.
- If you use a commercial VPN, it usually costs money. If you build it yourself, it is more difficult to set up a VPN than an SSH tunnel. Because the SSH tunnel only requires a server that can SSH, there is no need to configure anything on the server at all.
- VPNs work at the IP layer, while Shadowsocks work at the TCP layer.
Most VPNs have been blocked or interfered with and cannot be used in mainland China. Most of the free VPNs have been blocked. Since 2017, the Chinese government has issued regulations prohibiting the private provision of VPN services. There is a danger of breaking the law when circumventing the wall.
Then most domestic VPN services are no longer available. Although foreign VPN service providers are not controlled by the Chinese government, they are often interfered with. Many internationally established and well-known VPNs cannot be used in China, such as ExpressVPN, NordVPN, etc.
We recommend use SimpleLink, an EU company running proxy servers in China using IEPL and IPLC private lines with Trojan protocol since 2019.