China Internet censorship in 2023 - common methods to censor the internet part 2

Author
GoClickChinaIn the first part of the article, four common methods to censor online content are discussed: IP and Protocol-based blocking, Deep Packet Inspection-based blocking, URL-based blocking, and Platform-based blocking. We now continue to cover other commonly used techniques to block content on the internet.
DNS-based blocking
-
Affected users/services. The number of users and services affected by this kind of blocking may vary depending on the level at which this technique is applied. In the case of nationwide DNS blocking, this number can be considerably high.
-
Level of unintentional blocking produced. High/Very high. Since users are prevented from resolving certain DNS, the collateral damage is usually high. Think of Facebook, for example; in countries where this social network is banned, millions of users are affected by not being able to access the content. Another aspect to keep in mind is the poisoning of DNS records produced by some countries such as China which can block content even outside its borders. For more information about DNS censorship and the behavior of the Great Firewall of China, please read our related article.
-
Effectiveness in blocking content. This technique by itself is easy to evade so its efficiency is poor.
-
Can it be circumvented?. Yes, it can be evaded. There are several ways to circumvent this censorship. The simplest way to evade censorship for the average user is to use a VPN that encrypts the DNS query so that the server cannot read it and therefore does not apply the filters. Another more advanced technique is to manually point to another DNS resolver or to have a local list of the IPs of the websites you want to visit.
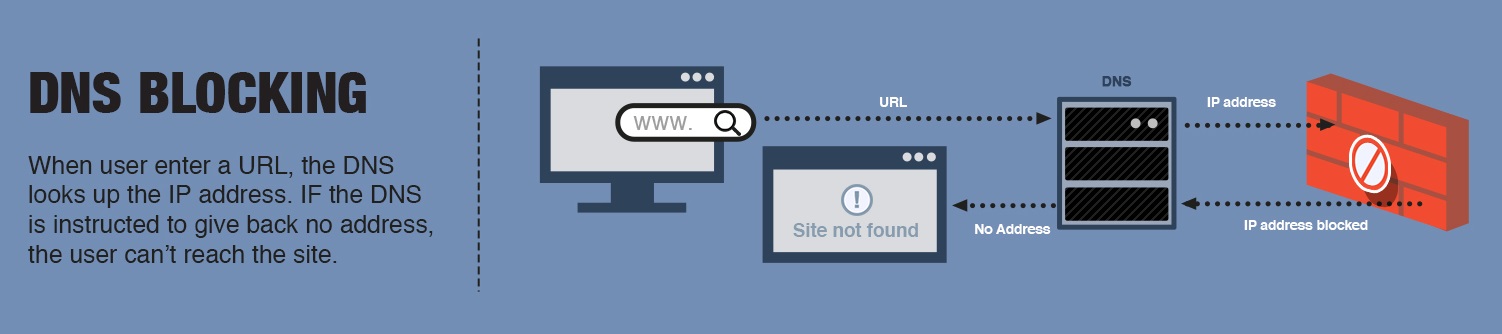
This is one of the most popular techniques for censoring Internet content. The reason is simple; the regulatory body only needs control over the DNS servers to apply the filters it wants. Maintaining a list of inappropriate domains is relatively simple, so many countries use this mechanism to apply the content controls they deem necessary.
However, the effectiveness of this blocking is debatable since, like URL-based and IP-based blocking, users can use a VPN to circumvent the filters. On the other hand, content creators only have to change the domain to circumvent this mechanism.
Network shutdown
-
Affected users/services. All users within the blocked zone will be affected by this method.
-
Level of unintentional blocking produced. Low/High. The level of collateral damage produced by this method is variable. For example, if the intention is to block Internet access to a specific city, this may cause neighboring towns to suffer the consequences. It all depends on the topology of the network.
-
Effectiveness in blocking content. High. Restricting Internet access to an area, city, or province is often very effective because users can only circumvent such restrictions if they have access to another service.
-
Can it be circumvented?. This type of blocking can only be bypassed if the user has access to an alternate network to access the Internet. For example, if the fiber-optic Internet service is blocked, it could be circumvented by using a 5G Internet service. However, given the extreme nature of this type of blocking, local services are often completely suspended, so the only viable alternative is often satellite Internet access.
Physically blocking access to the Internet is one of the most extreme censorship mechanisms available. For this reason, governments usually apply it only in cases of necessity or under very specific circumstances. Since Internet access is provided through ISPs, all the competent authority has to do is to request that service be blocked in a certain area. Generally, ISPs have nodes that serve certain areas, so the network topology determines how many cells/stations/proxies need to be shut down.
VPN blocking
-
Affected users/services. This kind of blocking only affects VPN users.
-
Level of unintentional blocking produced. Since the blockade is targeted at a specific service, the level of collateral damage is usually low. However, depending on the mechanism used by the regulator, ordinary users may experience slowdowns when surfing the Internet.
-
Effectiveness in blocking content. Low/Medium. Blocking VPN service providers is not simple. This is because identifying encrypted traffic requires a lot of resources. Moreover, VPN service providers are always innovating and looking for ways to circumvent detection.
-
Can it be circumvented?. Yes. From the user’s point of view, there is little that can be done. However, the service provider tends to constantly change its strategy with each software update, so users only have to wait in case they are blocked.
Attempting to block VPN providers is logical since it is thanks to them that the censorship mechanisms described above can be circumvented. There are different ways of blocking VPNs. One is to block the ports that VPN protocols usually use, although, as you can imagine, this is usually not very effective. Another way is to use IP-blocking for all servers identified as VPNs; however, this has the drawbacks described above. Simply changing the IP is enough to circumvent this censorship. One method that has proven relatively effective is that used by the Chinese government. On the one hand, the GFW uses deep packet inspection to try to identify VPN traffic and, on the other hand, has instructed ISPs to block individuals from using VPNs.

Manual and A.I. censorship
-
Affected users/services. The users and services affected will depend on the policy and strategy used by the regulator. For example, if a country considers certain content inappropriate, it can create a list of keywords that will be the focus of attention of both manual and automatic mechanisms.
-
Level of unintentional blocking produced. Variable. The degree of unintended damage caused by this type of censorship is variable since the results of this technique are usually fed to another blocking system (such as IP or URL blocking).
-
Effectiveness in blocking content. Once the IA has been trained, the effectiveness in detecting content prone to censorship is high (over 80%).
-
Can it be circumvented?. From the users’ point of view, the chances of their online comments being noticed by this type of censorship are low. However, for activists or publications that are not in line with local regulations, evading this type of mechanism is much more difficult.
This censorship mechanism is generally used to monitor social networks and news sites. In this sense, artificial intelligence and highly sophisticated algorithms are used to detect certain types of content and comments. Since AI can learn over time, it often works in combination with teams that perform censorship manually. This allows the AI to learn new patterns, keywords, and content susceptible to censorship. According to recent estimates, once the AI has been trained its effectiveness in detecting inappropriate content is greater than 80%.
Where is blocking happening?
Up to this point, we have discussed the mechanisms and techniques used globally to filter and censor content on the Internet. However, an equally important aspect is to know where this blocking occurs.
**Blocking or filtering on user’s devices. **One of the key points where content filtering can be performed is at the user level. Both security suites and parental control software have the ability to use local DNS blocking, IP blocking, URL blocking, or deep packet injection. Moreover, even without the user’s knowledge, Trojan horses can be used to install malware that fulfills this functionality.
Local network filtering. At a higher level, proxies or security appliances could be used to monitor all incoming and outgoing traffic on a local network. Such devices can be configured to use all the techniques described in this article, DNS blocking, IP blocking, URL blocking, and deep packet injection. This is a common enterprise-wide practice to filter unwanted traffic and protect devices from malware and viruses. However, nothing prevents national regulators from installing such devices in schools, government agencies, libraries, entertainment centers, and other points of interest.
Internet Service Providers (ISPs) - Hosting/cloud provider. In countries such as China, India, the United States, and Iran it is common practice to require ISPs and hosting providers to install devices that allow DNS filtering at the DNS resolver level. This is one of the most critical points in the censorship scheme since in one way or another, users must use the ISP to access the Internet.
Search engine or platform provider. As explained in the previous section, service providers such as Google, Bing, Bai, Yahoo!, Facebook, and Twitter often work in conjunction with local authorities to filter certain types of content.
Overview of how content is blocked online
In this section, we will explore with an example how the content filtering mechanisms come into action. For this purpose, let us assume that a search engine is used to search for the word “bomb”.
-
Platform-based blocking. If you are using a search engine with filtering, you may see a message like “no result found for bomb”. Otherwise, if you are using a “clean” search engine, you will see a list of results. Let’s say you decide to click on the example.com website.
-
DNS-based and IP-based blocking. Once the first barrier is overcome, when you click on example.com your device queries the DNS resolver to find out the IP of the website. At this point, you can be blocked by either DNS-based filtering or IP-based filtering depending on the type of mechanism used by the regulator, the blacklist, and the keywords used. That is, if the word “bomb” is part of the keywords or if the example.com IP is blacklisted you will not be able to access the content.
-
URL-based and Deep packet inspection blocking. Let’s assume for a moment that you manage to overcome filtering at the DNS resolver level. In that case, you will be able to successfully connect to example.com and request the page corresponding to the word “bomb”. At this point, two types of blocking can be triggered. If the page example.com/bomb is on the blacklist of URLs then your connection will be blocked. On the other hand, if the page is not on the URL blacklist but the keyword “bomb” is on the keyword blacklist, its connection may be interrupted by deep packet inspection based filtering.
Conclusion
In this article, we have delved into the most common methods of censoring and filtering online content used by authorities globally. Given the multitude of techniques used together, it is clear that achieving visibility in countries with strong censorship mechanisms can be a challenge.


